GoBruteforcer Botnet Targets Crypto Infrastructure via Weak Passwords
A new wave of cyberattacks is aggressively targeting cryptocurrency and blockchain infrastructure. At the center of this campaign is the GoBruteforcer botnet, which compromises exposed Linux servers by exploiting weak or default credentials. Once breached, these systems are absorbed into a wider botnet used to scan and attack additional targets across the internet.
Security researchers report that the attacks rely on simple but highly effective techniques rather than sophisticated exploits, highlighting ongoing failures in basic security hygiene across the crypto ecosystem.
Key Findings From Security Research
Compromised Services and Infrastructure
Researchers observed a coordinated campaign targeting commonly exposed services, including:
- FTP servers
- MySQL and PostgreSQL databases
- phpMyAdmin interfaces
- Poorly secured Linux-based web stacks
Attackers gain initial access through reused or default credentials, often left unchanged after deployment. Once inside, they deploy PHP web shells and IRC-based bots, allowing remote control of infected machines and automated scanning for new victims.
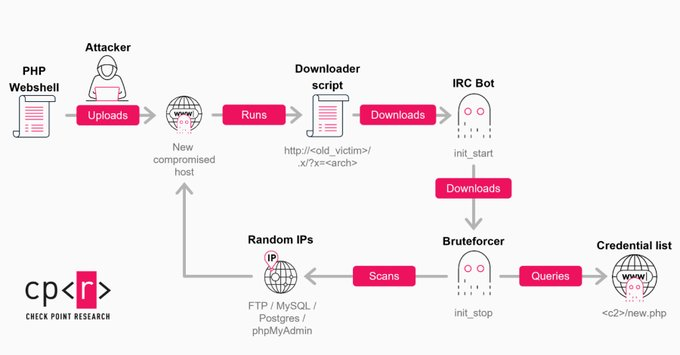
Root Causes Behind the Campaign
According to Check Point Research, two systemic issues are driving the spread of GoBruteforcer:
- Widespread reuse of AI-generated server configuration guides that include default usernames and passwords
- Continued use of outdated software bundles such as XAMPP with little to no security hardening
These practices create an ideal environment for automated brute-force attacks at scale.
Evolution of the GoBruteforcer Botnet
Early Discovery and Malware Lineage
GoBruteforcer was first documented by Palo Alto Networks Unit 42 in March 2023. In September 2025, Lumen Technologies Black Lotus Labs linked the malware to the broader SystemBC ecosystem, showing signs of infrastructure and tooling overlap.
Technical Advancements
Check Point identified a more advanced Golang-based version of GoBruteforcer featuring:
- Obfuscated IRC command-and-control bots
- Improved persistence mechanisms
- Process-masking techniques to evade detection
- Continuously updated credential lists with crypto-focused usernames
These improvements significantly increase the botnet’s stealth and longevity.
Targeting Blockchain Assets
Direct Attacks on Crypto Ecosystems
Investigators uncovered a particularly alarming behavior: one infected server was actively scanning TRON addresses using the Tronscan API to identify wallets holding non-zero balances.
As noted by Check Point Research, this indicates deliberate targeting of blockchain assets rather than random internet-wide scanning.
This activity aligns with broader threat intelligence reports from GreyNoise, which recently highlighted mass probing of misconfigured proxy servers and exposed AI infrastructure.
Why This Matters
The GoBruteforcer campaign demonstrates how automated botnets can exploit basic security failures at scale. For crypto projects, the risks extend beyond server compromise to potential theft, data exposure, and infrastructure abuse.
As blockchain adoption grows, attackers are increasingly focused on crypto-native targets, treating weak credentials and exposed services as low-effort, high-reward entry points.
Outlook for 2026
If current trends continue, botnets like GoBruteforcer are likely to:
- Expand further across crypto and Web3 infrastructure
- Integrate deeper wallet-scanning and asset discovery tools
- Target cloud-hosted blockchain services and developer environments
Without widespread improvements in credential management and server hardening, automated attacks will remain a persistent operational threat.
Sources:
- Check Point Research
- Palo Alto Networks Unit 42
- Lumen Technologies Black Lotus Labs
- Original reporting via The Hacker News



